Dumping Firmware with Bus Pirate v3.6 via USB
buspiratefirmware dumping
Introduction:
Utilizing the Bus Pirate and SPI interface is an effective method for extracting firmware from hardware devices. This is particularly useful in scenarios where direct firmware downloads are not an option.
Requirements:
- Bus Pirate: A tool for interfacing with hardware devices at the protocol level.
- Operating System: Ubuntu 16.04 or other Linux distributions.
- Flashrom Tool: A utility for reading, writing, verifying, and erasing flash chips.
- SOIC Cable Pin 8: Connects the EEPROM chip.
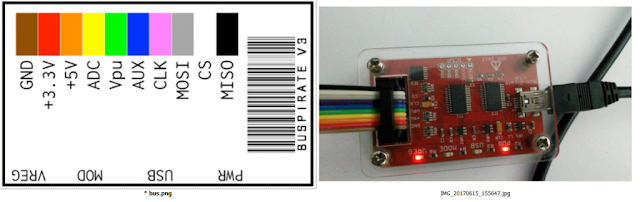
- Bus Pirate Connectors
Hardware Example: Binatone DT 850W Wireless Router:

The Binatone DT 850W wireless router used for firmware dumping.
What is EEPROM?:
EEPROM stands for Electrically Erasable Programmable Read-Only Memory. It is a non-volatile memory used in electronic devices to store small amounts of data, allowing individual bytes to be erased and reprogrammed.
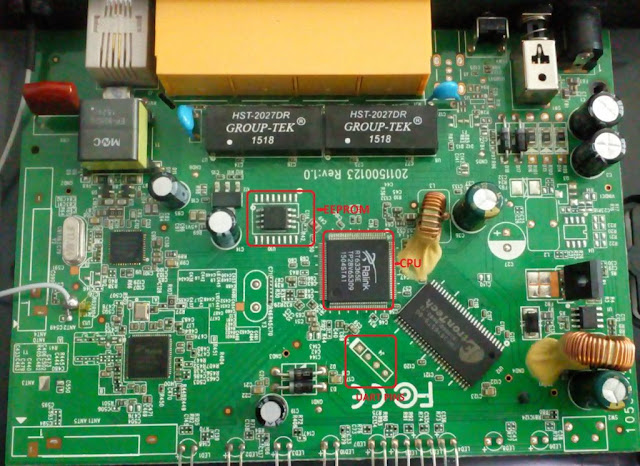
EEPROM chip on the circuit board.
Preparing for Firmware Dumping:
1. Connecting Bus Pirate to EEPROM Chip:
Use the Bus Pirate and the SOIC Pin 8 connector to establish a connection with the EEPROM chip. Ensure that the red wire connects to pin 1 of the EEPROM chip, identifiable by a round mark.
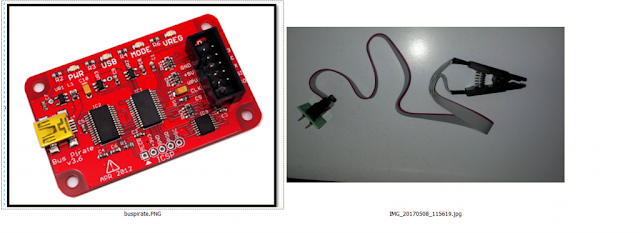
Bus Pirate and SOIC Pin 8 connector setup.
2. Bus Pirate and SOIC Cable Setup:
Arrange the Bus Pirate and SOIC cable according to the provided diagrams to ensure correct pin connections.
3. Connection Verification:
Check the VREG and PWR indicators on the Bus Pirate to ensure a proper connection.

Verifying the connection on the Bus Pirate.
Firmware Dumping Process:
Step 1: Initial Setup
- Ensure the RED wire is connected to pin 1 of the EEPROM chip. A round mark on the chip identifies pin 1.
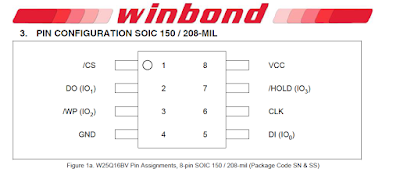
Identifying pin 1 on the EEPROM chip.

Bus Pirate wired to the EEPROM chip.
- Connect the SOIC cable to Bus Pirate Pins as shown below:
SOIC cable connected to the Bus Pirate pins.
- Use this extra connector to the SOIC cable to identify the pins easily:
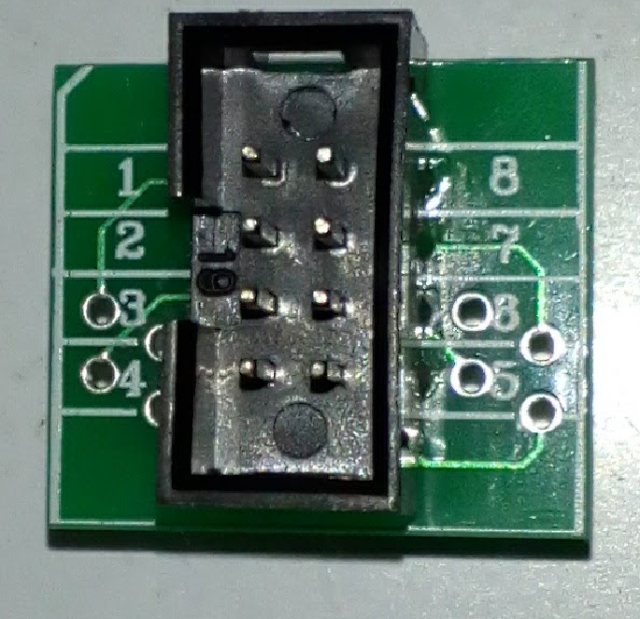
Extra connector aiding in pin identification.
- After connecting the Bus Pirate to SOIC pin 8, it should look like this:
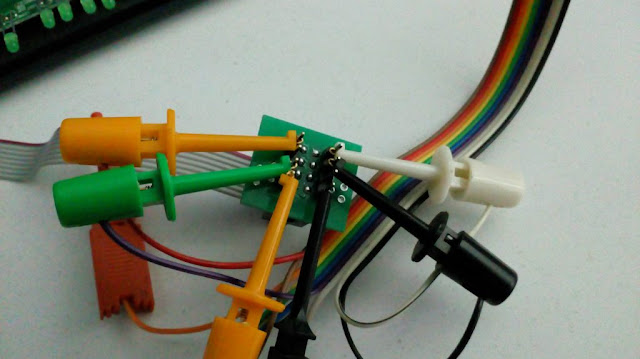
Complete setup of Bus Pirate and SOIC connector.
- A perfectly made connection to the device:
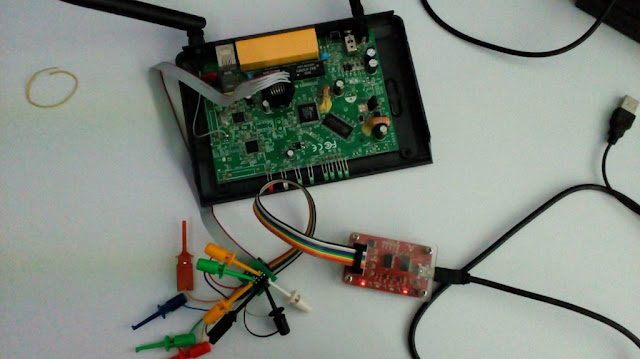
A perfectly established connection for firmware dumping.
Step 2: Identifying the EEPROM Chip
Execute the following command to identify the connected EEPROM chip:
sudo flashrom -p buspirate_spi:dev=/dev/ttyUSB0 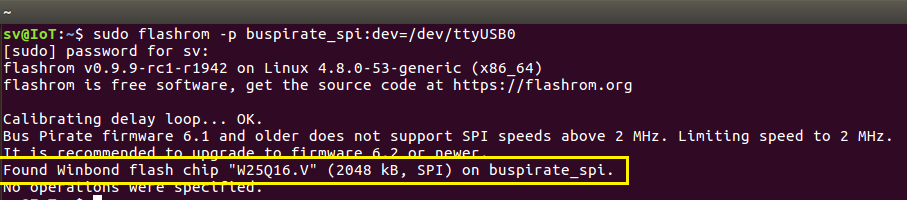
Command execution for identifying the EEPROM chip.
Step 3: Dumping Firmware
- Execute the following command to dump the firmware from the chip to a binary file:
sudo flashrom -p buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -c <Chip name> -r <Filename.bin> 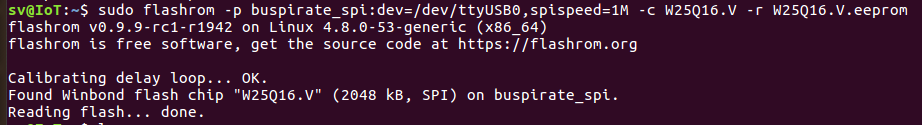
Dumping firmware from flash chip.